HIPAA Compliance Testing Checklist
Every software built for medical institutions or operating within the medical industry that functions in the USA or handles medical data of US citizens must comply with the Health Insurance Portability and Accountability Act (HIPAA). Started on August 16, 1996, the HIPAA aims to provide patients with healthcare portability and control of health information.
The volume of sensitive data processed by health software has grown exponentially with the rise of telemedicine and mobile health apps. Because medical data is one of the most valuable assets, healthcare applications have become the prime target of attacks such as ransomware, phishing, data theft, and malware.
Now, HIPAA compliance has evolved from just a regulatory requirement to a defense against breaches, lawsuits, and reputational damage. Complying with HIPAA means your software has enhanced data security, is protected from legal issues, handles patient data securely, and follows global data protection standards.
While complying with HIPAA is mandatory, it does not stop an application from being released without complying. However, if a complaint is filed against such an app or authorities are notified regarding non-compliance, the company can face severe penalties.
Penalties for HIPAA Violations
In 2020, Premera Blue Cross (PBC), a health insurer in the USA, was fined $6.85 million by the Office of Civil Rights due to a HIPAA violation that resulted in the data breach of over 10 million people. However, not every violation is equal, as violations are divided into civil and criminal categories.
Civil Violation
Violation Penalty An individual who violates HIPAA unknowingly. $100/violation with an annual maximum of $25K for repeated violations. Violation due to reasonable cause and not willful neglect. $100/violation with an annual maximum of $100K for repeated violations. Violation due to willful neglect but rectified within 30 days. $10K/violation with an annual maximum of $25K for repeated violations. Violation due to intentional neglect without taking any corrective measures within 30 days. $50K/violation with a maximum of $1.5 million annually Criminal Violation
Violation Penalty Willfully obtaining and disclosing protected health information $50K and up to a year in jail. Attaining PHI under false pretenses. $100K and imprisonment for up to 5 years. Obtaining PHI to sell, transfer, or use it for personal gain. $25K with imprisonment for up to 10 years.
It’s always said prevention is better than a cure. If your goal is to prevent such penalties, medical software security testing is your best friend here. Appropriate QA testing involves performing various tests, including penetration, security, and non-functional testing, protecting PHI, and strengthening users' trust in your application.
Though QA testing is an integral part of being HIPAA compliant, it is not the only factor. If you also have the question, ‘How to test HIPAA compliance?’ In that case, this article will be your HIPAA compliance checklist for healthcare software, highlighting the key information needed to become compliant.
Understanding HIPAA Requirements for Software
The first part of this HIPAA-compliant software checklist is to understand the requirements set for HIPAA. To be compliant, your software needs to meet the dedicated requirements, which are categorized into four rules:
1. Privacy Rule
The HIPAA Privacy Rule states that every covered entity, including healthcare providers, health plans, healthcare clearinghouses, and business associates such as software vendors that handle PHI, should protect the medical records of every individual.
In terms of software, this rule directly impacts how the application is designed regarding data access, user permissions, patient rights, and audit capabilities. To ensure compliance, every healthcare software must meet the following:
- Always ask for patient consent before storing data. Moreover, the application should track and log when patient consent is obtained, what it covers, and how long it remains valid.
- Patients can access and attain copies of their data whenever they want.
- Appoint a privacy officer who will monitor compliance and ensure the necessary privacy policies are implemented.
- Patient data should be shared only for research, care, and legal purposes.
- Every third-party or associate of the entity handling PHI must adhere to the privacy protocols.
- Implement role-based access controls to ensure that only patients, providers, and admins can access the specific data and features necessary for their roles, avoiding unauthorized access.
2. Security Rule
The Security Rule emphasizes how PHI is safeguarded, while the Privacy Rule controls who may access PHI. The healthcare application or software must apply physical, technical, and administrative safeguards to guarantee the security, integrity, and availability of electronic protected health information (ePHI). The HHS has segregated risk assessment guidelines into three sections:
Physical Safeguards:
- Limit physical access to electronic systems.
- Develop policies to define appropriate usage of systems and workstations that can access ePHI.
- Stringent policies regarding the removal or movement of hardware storing ePHI in or out of the facility.
Technical Safeguards:
- Implementing access controls for ePHI.
- Implementing authentication mechanisms for safer logins and data protection.
- Adding security layers to data transmission.
- Implementing hardware and software to record the activity of systems storing ePHI.
- Implementing access controls for ePHI using frameworks supported by IAM solutions like Okta or Auth0.
- Implementing centralized log management to record hardware and software activity of systems storing ePHI using ELK Stack, Splunk, or Datadog to ensure real-time visibility and audit readiness.
Administrative Safeguards:
- Identifying risks associated with ePHI and implementing security measures.
- Hiring a designated security officer to create and implement Security Rule policies.
- Implementing policies for authorization to the workforce working with ePHI.
- Evaluating policies and procedures frequently to ensure they meet Security Rule requirements.
- Always have a written BAA before letting any third party access ePHI.
- Offering awareness and training sessions to the workforce.
- Creating a disaster recovery plan.
- Assessing third-party vendors' access to ePHI, verify their security controls, and document their compliance through due diligence and BAA.
3. Breach Notification
Even after implementing the best practices, the possibility of facing a breach still remains. The Breach Notification rule implies that, after discovering a breach, covered entities and business associates must report it immediately, and any delay, due to any reason, should not exceed 60 days. The following entities should be notified in case of any breach:
- Individual users whose data has been compromised.
- In case the breach affects over 500 patients, the covered entity should notify media outlets serving the State of jurisdiction.
- Along with the media, the covered entity must also report the breach to the Secretary through the HHS portal. In case the breach affects fewer than 500 users, the covered entity can notify the Secretary annually.
- When the source of breach is a third-party associate, they are liable to notify the covered entity along with all the information, including details of affected individuals, if possible.
4. Business Associate Agreement
A business associate is any third-party service provider that a covered entity may use to create, receive, preserve, or transmit protected health information (PHI). HIPAA's legal mandate, the Business Associate Agreement (BAA), controls how business associates treat PHI on behalf of covered entities. The BAA states that business associates should also meet the desired rules of HIPAA, and failing to do so can result in penalties for the covered entity.
Pre-Testing HIPAA Compliance Assessment
Rather than moving directly to healthcare software testing for HIPAA compliance, the right course of action is to conduct a pre-testing. The pre-testing stage involves aspects including documentation review, PHI data flow, evaluating and managing risk, and identifying critical testing points for the app. But first, let’s move to documentation.
- Documentation Review:Documentation is among those highly confusing areas of HIPAA compliance. To make things easier, here is a list of common documents that you need to prepare:
- Privacy Policies and Procedures: Make sure to document your privacy policy, where you need to develop guidelines based on the entities that can access PHI. Include what, when, who, and how someone can access the PHI.
- Business Associate Agreements: If your software uses third-party services that access PHI (like cloud providers or analytics tools), signed BAAs are mandatory. Review each agreement to confirm it includes breach responsibilities, security expectations, and the scope of data use. Missing or outdated BAAs are a red flag in any HIPAA audit.
- System and Architecture Documentation: Cloud infrastructure notes, database schemas, API references, and thorough system architecture diagrams are essential as these documents provide crucial information for both compliance and testing teams and outline how PHI moves through your application, where it is stored, and how it is protected.
- Audit Logging and Review Policy: HIPAA’s Security Rule testing requires activity tracking. Make sure your audit policy defines what events are logged (such as logins and data changes), retention duration, and how logs are secured and reviewed. Logs should be immutable and regularly monitored for unauthorized access attempts.
- Incident Response Plan: Lastly, have a clear and tested breach response plan. It should outline how to detect, respond to, and report a PHI breach within HIPAA’s 60-day window. Assign clear roles, communication steps, and escalation paths so your team isn’t scrambling in a real-world incident.
These are some of the generic documentation requirements used for healthcare software. However, connecting with a professional can help you understand the requirements for your software.
Risk Management and Data Flow Mapping
Apart from documentation, you need to start data flow mapping to understand how data flows within your software. You need to identify every individual or entity that can access PHI, the ways to transfer and store data, and the types of PHI involved. To begin data mapping, start with the data source and track the path of data travel as it moves within the software.
To make data flow easier, you can use tools including Lucidchart, Microsoft Visio, Azure Diagrams, and Swagger.
Once mapped, you need to access each point in the flow to identify any underlying vulnerability within the system. These vulnerabilities could be unsecured endpoints, weak access controls, a lack of encryption, or an insecure firewall. To make things easier, you can use a risk assessment framework such as NIST or HSS guidelines to identify, categorize, and prioritize risks based on likelihood and impact.
When selecting a suitable risk framework, several key factors should be taken into account, including data type (structured or unstructured), deployment model, acceptable risk level, integration with third-party APIs, remote access support, and scalability options. These factors will help you determine whether you need frameworks offering detailed threat modeling and access control analysis.
Identifying Critical Testing Points in the Application
After mapping PHI data flows and conducting a breach risk assessment, the next step is to pinpoint areas in your application that directly interact with sensitive health information and enforce HIPAA-related safeguards.
These points typically encompass components responsible for user access, data transmission, storage, logging, and interactions with third parties. The goal is to identify where failures could lead to unauthorized access, data breaches, or non-compliance. Prioritizing testing in these areas will help to guarantee patient data protection and regulatory compliance.
By isolating these high-risk zones early, your test planning will become more focused, efficient, and aligned with real-world HIPAA enforcement priorities without being distracted by low-impact components.
Additionally, you can determine the test scope with the information attained from data mapping. Once you understand where PHI enters, moves through, and exits your system, you can define what parts of the app need the most rigorous testing. These may include:
- Modules where users input or access PHI
- Backend services or APIs where data is transmitted between systems.
- Data stores where PHI is saved or archived.
- Third-party interfaces
- Audit log systems that track actions.
To prioritize testing, you can consider the following:
- Volume of PHI processed in a module.
- Complexity of logic
- Past failure points or known vulnerabilities from earlier assessments, if any.
- External exposure, including APIs and third-party services.
For example, if mapping reveals that PHI passes through a public-facing API without encryption or proper access controls, that API becomes a critical test target. By aligning test coverage with data flow maps, your efforts focus on areas where HIPAA violations are most likely to occur.
HIPAA Compliance Testing Checklist
Software testing is integral to achieving HIPAA compliance for your application, as an insecure application increases the possibility of breaches and data leaks. Performing the following tests will allow you to understand healthcare software testing requirements and accomplish the HIPAA guidelines while maximizing security.
1. Access Control Testing
Unauthorized access events accounted for 18.2% of all HIPAA breaches recorded by healthcare entities in 2023. HIPAA mandates that organizations implement secure practices to protect ePHI; however, it is unclear what specific actions should be taken to achieve this goal. You can accomplish this through access control testing, where you will add additional security layers in the software to access the data, hence protecting it. Here, you need to test:
a. User Authentication Mechanisms
How does the user log in to the program? Can they access it without the correct credentials? Is the 2FA working correctly? Is there a mechanism for account lockout after repeated failed attempts to prevent brute-force attacks? Testing all these will help you ensure that only the right entity can access the data.
Apart from that, the following test scenarios can further expand the test efficacy.
- Simulating failed login attempts to trigger account lockout.
- Checking 2FA bypass risks by intercepting OTPs or using expired codes.
- Testing expired or reused password reset links.
- Validating session tokens for replay attacks via Postman or Burp Suite.
b. Role-Based Access Control Validation
Rather than granting everyone access to all the data, you need to implement role-based access control mechanisms, where only people who need to access specific data can do so. Here, you need to test that users can only access data authorized to them instead of all the information.
Here, you can run these test scenarios to test RBAC:
- A patient cannot view another patient’s medical history.
- A nurse cannot access financial records.
- A receptionist can schedule appointments but not view clinical notes.
- A doctor can access lab results, treatment plans, and medications for their patients only.
- An admin can manage users but cannot read PHI directly.
c. Session Timeout
If the user has been logged in for a long time without activity, the session timeout should kick in and force the user to log out, reducing the risk of unauthorized use. Test whether inactive sessions expire after a defined period.
For the optimum outcome, you need to test the following:
- Inactivity timeout or force logout after a specific idle time.
- Absolute session lifetime and force re-login after a specific time, even if active.
- Forced logout on logout from another device or browser.
- Ensuring no access is possible via the browser back button after logout.
- Testing if session cookies are cleared and not stored in the browser cache.
Through Selenium, you can automate session timeout simulation by triggering inactivity delays and observing session expiration behavior.
d. Emergency Access Procedures
HIPAA requires the healthcare software mechanisms to let authorized personnel access data in case of system outage, patient crises, natural disaster, or any other emergency without compromising security controls. Testing should verify whether emergency access is possible without relying on standard authentication paths, but it still requires proper authorization and logging.
2. Data Protection Testing
The worst year the sector has ever seen was 2023, with over 168 million healthcare records exposed, stolen, or impermissibly shared. This number not only beats past years but also showcases the need to meet healthcare software testing requirements and adopt a more aggressive attitude toward protecting PHI.
Data protection is the foundation of HIPAA-compliant software testing, focused on ensuring that ePHI is handled securely. Here, the spotlight is on verifying that data is not just stored securely but also transmitted, processed, and disposed of in ways that minimize the risk of exposure or breach. A strong PHI data protection testing strategy should include the following areas:
a. Encryption Testing for Data in Transit and Data at Rest
Data encryption is among the mandates in HIPAA when dealing with ePHI, as it is critical to safeguarding PHI, both when it is stored and when it is transmitted.
Healthcare data encryption validation and testing involve verifying that strong data encryption standards are correctly implemented to protect sensitive information. The encryption is tested to ensure that it is capable of protecting sensitive data. The industry benchmarks include TLS 1.2 or higher for data in transit and AES-256 for data at rest.
Algorithm verification, speed of encryption, and latency are among the key tests involved here. Hashcat or OpenSSL are the top tools that can be used to simulate attacks on data at rest and help verify whether encryption algorithms are correctly implemented. Using these tools, you can
- Attempt decryption using weak or outdated ciphers to confirm they are disabled.
- Simulate brute-force attacks on encrypted backup files.
- Identify that encryption keys are stored securely and not hard-coded in the software.
For data in transit, Wireshark or Burp Suite are essential tools for intercepting and inspecting network traffic. You can attain the right outcome by:
- Checking if the data sent over the internet is encrypted using HTTPS or TLS 2.1.
- Testing how your software handles invalid or expired encryption certificates.
- Detecting if any PHI is sent in plaintext or without proper certificates.
b. Data Integrity Testing
As the data travels within the software, it can be altered or corrupted if there is an underlying vulnerability. Data Integrity testing includes evaluating the database to ensure it handles the data as anticipated without showing signs of corruption or change in data. To test the data, you need to:
- Ensure that you can create, remove, or alter data.
- Compare the hash values of data before and after storage or transmission.
- Test that the data is compatible with various versions of OS and hardware.
- Check whether the data is saved successfully in the database.
- Use tools such as WinMerge or HashMyFiles to help identify any changes to data.
Since the application stores, transfers, and processes PHI, there's a risk of data corruption. To make sure your application can manage data corruption, you can:
- Simulate network interruptions during data uploads or transfers to see if broken data is saved.
- Alter or delete the test records in your database manually using a DB editor.
- WinMerge or HashMyFiles can identify changes made to data, allowing you to determine whether the data is corrupted.
- You can also add a corrupted file to the system and determine whether your software is capable of identifying it.
c. Backup and Recovery Testing
You need a data backup ready in case of unforeseen circumstances, such as a natural calamity or ransomware attack. HIPAA has mandated that every healthcare software should have a data backup. Testing the backup and recovery mechanisms ensures that you can restore data whenever you face a threat, allowing users to have uninterrupted access to their data.
Here, you may need to perform the following actions:
- Test backups at least quarterly in staging environments to simulate full restoration.
- Simulate partial recovery as well as full-system recovery to test data recovery mechanisms.
- In some cases, you may need to roll back to a previous version. Test the rollback feature by intentionally deploying an older backup, validating that the software can revert to the previous version without data corruption or broken functionality.
- Test backup scenarios for different types of incidents, including but not limited to accidental deletion, ransomware attack, or hardware failure.
- Perform rollback testing by intentionally deploying an older backup, validating that the system can revert to the previous stable state without data integrity issues or broken functionality.
- Ensure that access controls and audit logs are preserved during recovery.
3. Audit Controls Testing
Healthcare software must log, monitor, and analyze user and system activities to become HIPAA compliant. You need to test these controls to validate that your system records essential events accurately and securely, and follows the compliance audits and internal investigations. According to HIPAA guidelines, you are required to maintain logs for a minimum of 6 years. To achieve this, you need to:
a. Audit Log Functionality and System Event Recording
A healthcare software includes several events such as user logins, logouts, access to PHI, data modifications, permission changes, failed login attempts, and admin actions. Audit log functionality testing focuses on triggering these events intentionally and verifying that each is recorded in accordance with audit logging requirements, including correct timestamp, username, event description, and device information. The logs are not limited to patients but also for workforce members.
HIPAA compliance has mandated that each login in every healthcare software should be immutable, meaning once an entry is created, it cannot be modified or removed from the log. Testing log immutability involves:
- Attempting modification test where you need to trigger a user event and try to alter the corresponding log entry through the backend. Ultimately, you need to verify whether the modification has been declined or logged.
- You can also use a log management tool such as Graylog or Splunk to delete a log entry and confirm if the system prevents deletion and logs the attempt.
- Using a Write-Once, Read-Many (WORM) compliant storage allows you to ensure that the data is written only once and can be read many times.
b. User Activity Tracking
As HIPAA requires that all user actions related to PHI be traceable, software must record what happened, who did it, when, and from where. Testing this involves analyzing log entries to ensure that every user action, such as viewing, editing, or deleting data, can be linked to a specific, authenticated user session.
c. Reports Generation and Integrity
Merely having logs is insufficient, as they must be usable for compliance and security purposes. Your system should generate reports based on time, users, and event types. Also, the reports should reflect actual logged data without gaps or tampering. Digital signatures, hash checks, and access controls on generating reports, among others, are the top features you need to test to ensure that the reports are tamper-proof and maintain legal admissibility.
ELK Stack, Graylog, and Splunk are the top tools that will allow you to streamline the reporting by generating structured audit reports, implementing tamper detection mechanisms, offering robust search and filtering capabilities, and exporting logs for audits.
4. Transmission Security Testing
In 2023, Managed Care of North America (MCNA), a dental insurance agency in the USA, reported a breach in its internal IT network due to a malicious code by the LockBit ransomware group, compromising the data of 8.9 million users. To protect against such situations from happening, healthcare software must have defenses against unauthorized interception or modification of PHI during transmission. As ePHI is transferred through various mediums, it is necessary to test data transmission methods, including email, private networks, APIs, mobile devices, and other similar channels.
a. Secure Communication Protocols
Using robust, industry-standard encryption is the cornerstone of transmission security protocols. Verifying that all data in transit, including between client apps, servers, APIs, and third-party services, is encrypted with TLS 1.2 or higher is the first step in the testing process. Weak encryption, expired SSL/TLS certificates, or incorrect configurations, such as allowing insecure HTTP connections in addition to HTTPS, are what testers search for.
Being one of the most widely used communication mediums, email encryption testing is a significant part of HIPAA compliance, and is used to protect information shared through emails.
For this testing, you can send test emails from your software to trusted external accounts and monitor if the email showcases encryption certificates or not. Moreover, you need to check if the information received is in the right format and not as gibberish.
Apart from that, security professionals can use network analysis tools to intercept the email communication between the sender and receiver and try to decrypt the content without the proper keys. If the encryption is working, the data will be unreadable.
b. Network Vulnerability Assessment
Testing an organization's internal network infrastructure allows testers to detect potential vulnerabilities and entry points for attacks. Your strategy for testing the network should involve scanning for open ports, outdated services, misconfigured firewalls, along with physical devices such as routers and switches. Here, the main priorities are verifying firewall rules, intrusion detection/prevention systems (IDS/IPS), and ensuring that PHI isn't exposed via unsecured VPN tunnels or unprotected communication layers.
To eradicate the possibility of unsecured VPN tunnels, you can perform VPN tunnel validation. Here, testers must check whether the VPNs are configured properly, use strong encryption protocols such as IPSec, and avoid split tunneling that could expose ePHI.
To strengthen vulnerability assessment further, you can utilize a breach simulation, in which you may mimic an internal ransomware infection. For instance, an outdated workstation may be exploited by an unpatched remote desktop protocol (RDP) vulnerability. The tester will trace whether the malicious traffic can bypass the firewall or access PHI over the network.
c. API Security Testing
Many software applications leverage APIs for communication between different modules or external systems for better functionality. By testing APIs, you ensure that PHI exchanged through APIs is highly secured through encryption, rate limiting, and strict access control while maintaining log activity. Furthermore, testers also validate that OAuth2 or other authentication verification mechanisms are enforced correctly and that APIs reject requests lacking proper authorization.
You can also use Postman, Apache JMeter, Swagger, and SoapUI to monitor if authentication is working correctly, if API block requests have proper credentials, and to simulate real-world API requests to evaluate how the systems respond. Using ZAP, RESTlet, or other API fuzzing tools can allow you to perform in-depth security checks.
d. Mobile Device Security Testing
With every leading healthcare app having a smartphone application, testing the security of data transmission from mobile devices is essential. Moreover, HIPAA has mandated that every healthcare mobile app accessing or storing PHI should be secured. To achieve that, you need to verify that the mobile app implements encrypted communication, does not store ePHI locally without encryption, and resists interception through different techniques.
OWASP Mobile Top 10 provides essential guidelines highlighting the top vulnerabilities. Combine these guidelines with mobile testing tools, including MobSF (Mobile Security Framework), Burp Suite, Appium, and Frida, to enhance the security of your healthcare mobile application.
Special Considerations for Different Healthcare Applications
Not every healthcare application comes with the same functionality. Some might be specific to insurance, while others are dedicated to a healthcare facility. While attaining HIPAA compliance is similar in some ways, there are differences that should be considered.
For a quick comparison, you can refer to the following table:
| Compliance Element | HER Systems | Telemedicine Platforms | Patient Portals | Health Information Exchanges (HIE) | Mobile Health Apps |
| Access Controls | Required (role-based access) | Required (secure provider & patient access) | Required (patient & provider access) | Required (secure data sharing between entities) | Required |
| Audit Trails | Mandatory | Mandatory | Mandatory | Mandatory | Mandatory (if handling PHI) |
| Data Encryption | Required (during data transmission) | Required (for video, chat, and file encryption) | Required (secure messaging & records) | Required (secure data transfer) | Required |
| 2FA | Recommended | Recommended | Strongly Recommended | Recommended | Required (biometrics/PIN for apps with ePHI) |
| BAA | Required (with vendors) | Required (with telehealth vendors accessing PHI) | Required (with portal providers) | Required (with participating organizations) | Required (if third-party can access PH) |
Here is the detailed information on special considerations for various healthcare applications that you should know:
1. Electronic Health Record Systems
Electronic health record systems were introduced to provide better care to you, even if you prefer to consult with different medical professionals. As your EHR software will be storing ePHI, you need to put additional focus on protecting that data to comply with HIPAA. Actions such as:
- Implementing access control tools.
- Integrating an audit trail to let the user know about the access history of their data.
- Tokenization for better interoperability security.
- Encrypting data protects against data theft during transmission.
2. Telemedicine Platforms
Telemedicine has existed for quite a long time, but more and more users are inclining towards it, especially after the pandemic. However, they may pose security risks, which is why HIPAA has issued a few guidelines:
- Sometimes, software vendors who are not covered entities but have access to encrypted PHI and claim to be HIPAA compliant may not enter into a BAA, as they do not have the decryption key. However, telemedicine platforms that work with such software vendors have to consider them business associates.
- Telemedicine platforms must obtain consent from the patient to record ePHI.
- Conduct risk analysis on their platform using the HIPAA Security Risk Assessment Tool.
3. Patient Portals
Patient portals empower individuals to view their medical records, test results, and appointment details anytime, anywhere. However, this access comes with heightened responsibility. The key HIPAA requirements for patient portals include:
- Implementing stringent access controls, allowing only patients to access the data.
- 2FA should be added to every login to enhance security and authentication.
- Protect ePHI during transmission and ensure the data remains unaltered during storage and access.
- Integrating robust firewalls to protect against brute force attacks.
4. Health Information Exchanges (HIE)
HIEs made sharing patient data across two or more entities, including healthcare providers, seamless. Every HIE software needs to follow these guidelines to be HIPAA compliant:
- Creating a dedicated policy focusing on data usage, sharing, protection, and consent.
- Adding access controls and encryption protocols.
- Developing a breach response plan, showcasing the roadmap to take after a breach.
5. Mobile Health Applications
From appointment planners to chronic condition trackers, mobile health apps give healthcare on demand. Although handy, many of these apps process or store ePHI on personal devices or cloud servers, increasing their vulnerability to attacks.
- In addition to login credentials, add additional layers of security such as biometrics or PINs.
- Make ePHI and user data accessible 24/7.
- Adding remote data wipe capabilities to protect data in case of device theft.
- Take user consent before storing their data.
If you’re using third-party software development kits (SDKs) with access to ePHI, you need to make sure that they comply with HIPAA standards before integration. Using HIPAA-compliant SDKs such as SendBird and VideoSDK ensures that ePHI is secure from third-party SDK-related threats.
While integrating mobile analytics tools, review their data collection policies and restrict access to PHI-related screens to ensure they don’t collect and transmit confidential health data without user consent.
HIPAA Compliance Test Reporting
HIPAA compliance is not just about developing safe software, but also about proving it. Complying with HIPAA standards is easier when you have comprehensive test reports. Such reports also help organizations identify issues that may hinder them from becoming compliant. Software owners who employ a methodical and linked approach to compliance reporting not only confirm existing protections but also proactively identify, locate, and rectify errors before they escalate into violations. Let’s begin with the documentation required for compliance verification.
HIPAA mandates specific documentation as proof of compliance. These aren't optional as they're required for both internal accountability and external audits. At a minimum, your documentation must include:
- Risk Analysis Reports (as per 45 CFR §164.308(a)(1)(ii)(A))
- Business Associate Agreements
- Policies and Procedures relating to Privacy, Security, and Breach Notification Rules
- Employee Training Records
- Risk Management Plans (45 CFR §164.308(a)(1)(ii)(B))
- System Activity Review Logs
- Access Authorization Records
- Incident Response and Breach Notification Logs
From a software compliance testing standpoint, you also need to maintain:
- Test plans and methodologies used for HIPAA rule validation.
- Test case documentation for user authentication, encryption, audit logging, and access control.
- Test result records and any test failures.
- Evidence of remediation for identified vulnerabilities.
Furthermore, to improve the clarity of the documentation, you need to maintain version control, offering a clear history of all the testing activities. The test documentation should include updated information and reflect changes made after each test.
Include elements such as version numbers, information about changes made, the date of the update, and more. For a smoother process, you can use version control tools such as Jira, Git, TestRail, Vanta, and OneTrust, among others.
To ensure that documents are always audit-ready and updated, the best practice is to store them in a centralized compliance repository such as SharePoint or a GRC platform.
Tracking and Remediation of Compliance Issues
Documentation is one part of reporting, but one of the motives of documentation is to identify areas where you may be lacking, which may cause a hurdle in compliance. To identify hindrances, you need to start by tracking:
- Failed compliance test cases (weak encryption, misconfigured access levels).
- Configuration drifts from secure baselines.
- Unusual audit log patterns suggesting misuse or unauthorized access.
- Unpatched vulnerabilities identified during vulnerability scans.
- Third-party integration risks.
To make your test reports truly valuable, you need to document each failure with the correct information and context for the remediation action. In each test report, mention the test name, objective, system component under test, expected VS actual outcome, and severity level.
Once you pinpoint the issue, you may begin fixing it. Fixes may involve updating encryption protocols, modifying role-based access policies, or even redesigning how PHI is transmitted. Regular review of unresolved issues, especially high-severity ones, should be part of your compliance dashboard to prevent drift and ensure rapid closure.
Adding a remediation log that declares fixes applied, the team member responsible for the fix, the resolution data, and the validation results after the fix will not only support audit readiness but also build a traceable path from detection to resolution.
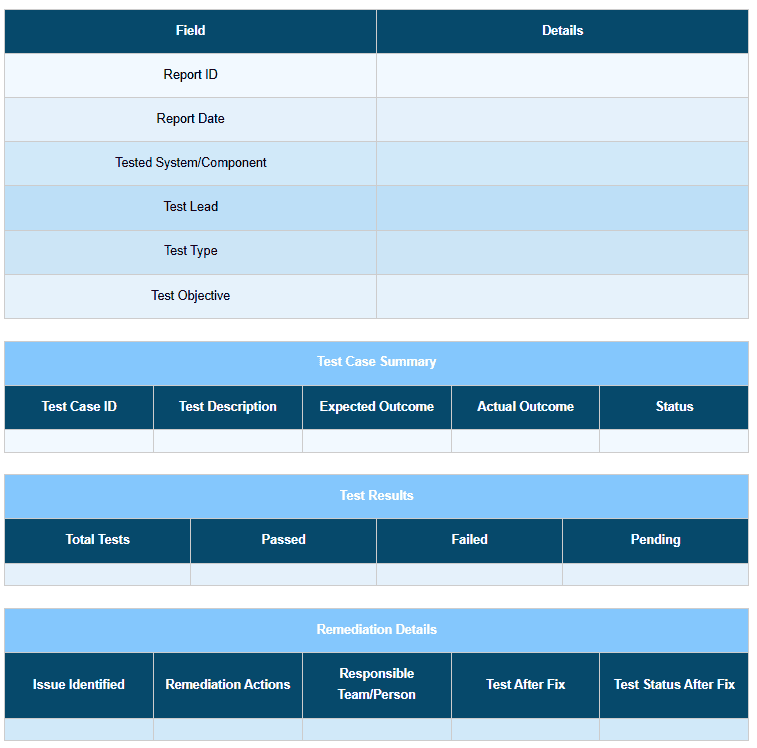
Refer to the below test case report template for a better understanding:
 OCR Audit Preparation
OCR Audit Preparation
One of the key aspects of HIPAA compliance is an audit by the OCR. OCR auditors are there not just to ask questions, but to evaluate your compliance documentation. Organize your documentation around the OCR's HIPAA Audit Protocol, which details particular implementation guidelines under every rule. Your audit-ready package should comprise:
- A summary of all test activities mapped to each HIPAA requirement.
- Copies of your risk analysis and mitigation plans.
- Logs of compliance issues with remediation evidence.
- Data backup and recovery plans.
- Training records to demonstrate that personnel understand and follow policies.
- Proof of ongoing monitoring activities.
Another way to prepare for an audit is through simulation. Conducting mock audits, internally or with a third-party HIPAA compliance expert, helps uncover gaps and ensures that your team knows how to respond under audit conditions.
Continuous Compliance Monitoring Strategies
Complying is one thing, but maintaining compliance is quite another. After achieving HIPAA compliance, your next task is to retain it, which can be accomplished through ongoing compliance monitoring.
You can leverage dedicated compliance tools such as Drata and Vanta to provide real-time alerts, reports, and integration capabilities. These tools can be integrated into CI/CD pipelines, enabling automated compliance checks during different stages of the SDLC.
Furthermore, you can scan the code for vulnerabilities and compliance standards, generate audit reports based on the factors collected throughout the process, and ensure zero-downtime releases, all of which enhance overall security and meet HIPAA regulations.
In addition, you also get compliance dashboards, offering you a centralized and real-time overview of your adherence to various HIPAA requirements by showcasing compliance scores, status of individual security controls, and any issues needing attention.
Complementing this feature are risk heatmaps, where you get a visual representation of compliance-related risks based on their impact, allowing you to assess and prioritize risk mitigation plans for continuous compliance monitoring.
You can also provide your staff with awareness and training, conduct routine audits, keep abreast of recent developments, adjust your plan and policies as necessary, and incorporate a feedback loop to evaluate the outcomes and identify areas for development.
Conclusion
HIPAA is not a destination but rather a continuous journey and a commitment. The risks and regulatory expectations change with new features, integrations, user expectations, medical practices, and threats that influence healthcare software. To retain compliance, the Department of Health and Human Services stresses the need for continuous breach risk assessments, policy reviews, and training.
Being a continuous process, it is always recommended to integrate HIPAA testing into the SDLC. From integrating security checks to healthcare application audit controls, blending all the testing actions into CI/CD pipelines is a must, not just before launch but with every update. By doing so, you will not only reduce compliance debt but also align the software with the HHS Secure Rule’s call for regular technical evaluations.
Just as medical advancements, HIPAA guidelines also continue to advance for the betterment of patient care. Regulatory changes, new threats, new mandates, and revised guidance often emerge without warning, and failing to comply may result in revocation of compliance. With that in mind, staying informed is non-negotiable. Timely updates and implementation guidelines come from trusted sources, including the HHS OCR website and the NIST Special Publications.
Keep in mind that complying with HIPAA is one task, and staying compliant is a separate and ongoing responsibility. You need to integrate these practices into your development, remain updated with the guidelines, and take all the healthcare application security testing measures to stay compliant.
Without a doubt, attaining and maintaining HIPAA compliance for healthcare software is daunting. ThinkSys, a software development and testing company in the USA, can provide you with all the guidelines, resources, and required assistance to attain HIPAA compliance.
Share This Article:







