Financial Application Testing: Critical Security and Compliance Requirements

Introduction
Apart from being a prime target for cyberattacks, the financial sector is also one of the most tightly regulated industries in the world. With data breaches now averaging $6.08 million per incident and compliance penalties climbing as high as 4% of global revenue, the stakes have never been higher. As financial software becomes more complex and interconnected, security testing becomes extremely critical.
This guide is built for security teams, compliance leaders, and engineering organizations dealing with security and compliance challenges. It provides a practical checklist for security testing in financial applications, covering everything from PCI DSS 4.0 and GDPR to DORA and SOX. Along the way, we’ll detail exactly what to test, why it matters, and how to provide evidence for auditors and regulators.
If your financial application deals with sensitive data, handles payments, or operates under regulatory oversight, this checklist is your roadmap for staying secure, compliant, and resilient.
Regulatory Framework for Financial Applications
In the financial sector, cybersecurity is a regulated obligation. Financial institutions operate under a dense and evolving network of laws and standards designed to protect consumer data, ensure the integrity of financial reporting, preserve operational resilience, and reduce systemic risk. These regulations spread across jurisdictions but are increasingly aligned in one area: they require verifiable, ongoing security testing and clear, auditable evidence of compliance.
This section outlines the most influential regulatory frameworks shaping cybersecurity requirements for financial software.
Overview of Key Regulations for Financial Software
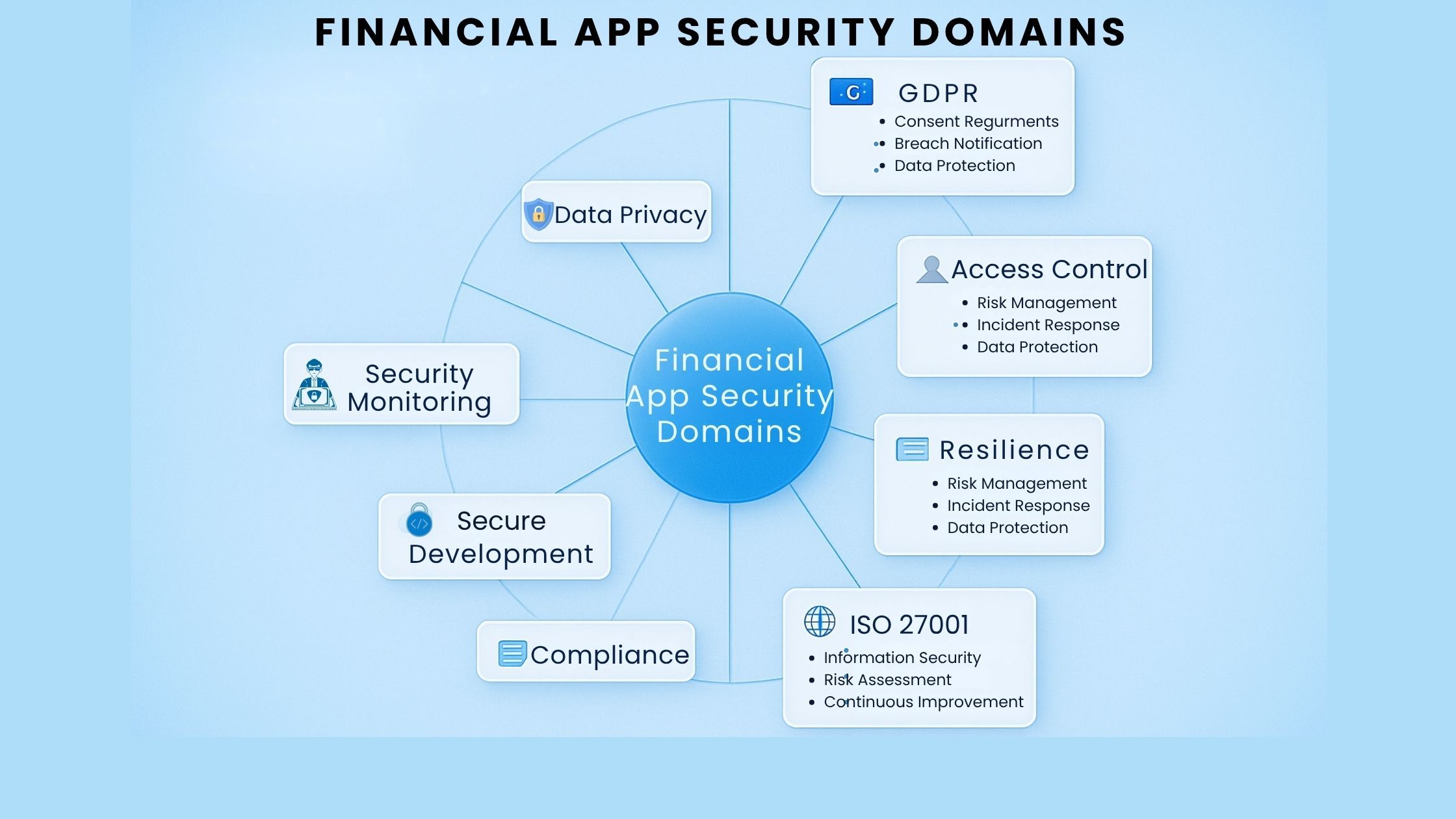
- PCI DSS (Payment Card Industry Data Security Standard)
Applies globally to organizations handling cardholder data Version 4.0, effective March 2024, introduces more than 60 new requirements aimed at increasing accountability and hardening controls across the payment ecosystem. These include:
- Stronger access control policies.
- Mandatory encryption and network segmentation.
- Quarterly vulnerability scans and annual penetration tests.
- Formal code reviews and continuous monitoring.
PCI DSS 4.0 also increases expectations for security governance. It requires firms to define roles, document procedures, and demonstrate testing outcomes. Failure to comply can result in fines, litigation, or loss of payment processing capabilities.
- Stronger access control policies.
- Sarbanes–Oxley Act (SOX)
Applies to publicly traded U.S. companies, primarily known for its focus on financial transparency, SOX also drives a wide set of IT controls that directly impact how financial software is developed and maintained. These include:
- Segregation of duties (SoD) to prevent conflicts of interest.
- Secure access management for systems that support financial reporting.
- Change control processes and audit trails for data integrity.
SOX violations may result in regulatory investigations, restatements of financials, or executive accountability under U.S. law.
- Segregation of duties (SoD) to prevent conflicts of interest.
- General Data Protection Regulation (GDPR)
Applies to any entity processing data of EU individuals. GDPR remains one of the most far-reaching data protection laws globally. It requires:
- “Appropriate technical and organizational measures” to protect personal data.
- Regular security assessments, including audits and penetration testing.
- Encryption, secure data storage, and strict access controls.
Non-compliance can lead to fines up to €20 million or 4% of global revenue, whichever is higher. GDPR emphasizes accountability and expects firms to document how data security risks are assessed, mitigated, and monitored over time.
- “Appropriate technical and organizational measures” to protect personal data.
- FINRA Regulations and SEC Cyber Disclosure Rules
Applies to U.S. broker-dealers, investment firms, and market participants. FINRA requires firms to implement risk-based cybersecurity programs that include:
- Ongoing vulnerability assessments and penetration tests.
- Documented response plans and evidence of remediation.
- Identity theft prevention programs.
- Reporting of specific incidents to regulators.
In addition, new SEC rules now require public disclosure of material cybersecurity incidents, making transparency not just a regulatory requirement but a reputational issue.
- Ongoing vulnerability assessments and penetration tests.
- FCA Regulations (United Kingdom)
Applies to UK-based financial firms and critical third parties. The UK’s Financial Conduct Authority (FCA) has expanded its security expectations to align closely with European resilience standards. Key mandates include:
- Regular penetration testing and vulnerability assessments.
- Disaster recovery and operational resilience testing.
- Mandatory reporting of major incidents to the regulator.
Beginning in 2025, critical third-party ICT providers will fall under direct FCA supervision, marking a shift toward regulating the full financial ecosystem, not just licensed institutions. This change mirrors the EU’s DORA framework and underscores a trend toward third-party risk accountability.
- Regular penetration testing and vulnerability assessments.
- DORA (Digital Operational Resilience Act – European Union)
Applies to financial institutions and critical ICT providers in the EU, starting January 2025. DORA introduces a formal and enforceable structure for digital resilience in the EU financial sector. Key provisions include:
- A mandatory annual security testing strategy.
- Threat-led penetration testing every 1–3 years for critical systems.
- Required remediation of findings and reporting results to EU supervisory authorities.
- Governance-level accountability for resilience programs.
DORA formalizes much of what was previously considered best practice, making operational resilience testing a legal obligation rather than a compliance recommendation.
- A mandatory annual security testing strategy.
- Other Global Cybersecurity Frameworks
In addition to the major regulatory anchors above, financial institutions are often subject to regional or sector-specific cybersecurity mandates. These include:
- PSD2 (EU): Security requirements for payments and open banking.
- MAS TRM Guidelines (Singapore): Technology risk management and incident reporting.
- RBI Cybersecurity Framework (India): Cyber resilience standards for banks.
- APRA CPS 234 (Australia): Information security obligations for financial services.
- NIST CSF / SP 800-53 (United States): Widely adopted frameworks for risk and control design.
- ISO/IEC 27001 (International): Best practices for information security management systems
These frameworks consistently emphasize data protection, access control, threat detection, system integrity, and auditability. For global firms, the challenge is not just to meet one framework but to harmonize compliance across jurisdictions without duplicating work or introducing risk.
- PSD2 (EU): Security requirements for payments and open banking.
How to Understand Which Testing Is Specified for A Certain Regulation
Every framework referenced above includes specific expectations for how security controls must be tested, validated, and documented. The nature of the testing may vary by scope and frequency, but the direction is the same: security is not valid unless it is tested, and test results must be provable.
Testing Area | Mandated or Expected by |
Technical scanning and penetration testing | PCI DSS, GDPR, FCA, DORA |
IT General Controls (ITGC) and Segregation of Duties (SoD) | SOX |
Incident response simulation & breach notification | GDPR, FINRA, FCA |
Evidence collection for audits and investigations | All frameworks |
Third-party system and operational resilience testing | FCA, DORA |
Some frameworks are now prescriptive. DORA, for instance, explicitly mandates threat-led penetration testing and regulatory reporting of findings. Others, like GDPR, are principle-based but still require rigorous technical testing and a documented ability to defend your choices during audits.
While the specific language and enforcement mechanisms differ, these frameworks are clearly converging around a shared operational model:
- Continuous testing over point-in-time assessments.
- Proof of remediation, not just detection.
- Executive and board accountability for cyber risk.
- Cloud, vendor, and infrastructure oversight, including internal systems.
Organizations that fail to meet these testing expectations will face penalties, eroding trust with regulators, partners, and customers.
On the other hand, firms that integrate evidence-driven security testing into their daily operations will be better positioned to meet compliance standards, reduce audit friction, and strengthen their long-term resilience.
Security Testing Requirements
With real-world consequences that now include multimillion-dollar breach costs, forced disclosures, and regulatory sanctions, organizations must approach testing as a continuous process embedded into the software lifecycle.
This section outlines core categories of security testing essential to financial systems, offering regulatory context, implementation guidance, and practical examples. 
Authentication Testing
Authentication is the first line of defense in any financial system. It ensures that only the right people, like customers, employees, and third parties, can access sensitive data and functionality, and that malicious actors are kept out. If you succeed at this, authentication protects against everything from phishing to credential stuffing and insider threats.

Regulators and industry bodies now treat strong authentication as non-negotiable. Multi-factor authentication (MFA) is required for high-risk actions under standards like PCI DSS 4.0 and PSD2, and frameworks like FCA and DORA call for routine validation of authentication controls during audit cycles. However, checking the compliance box isn’t enough. To stay ahead of evolving threats, authentication must be tested rigorously and continuously as systems, users, and attackers evolve.
Below are the key areas of authentication testing that every financial organization must address:
- Multi-Factor Authentication Validation
MFA is a regulatory and industry baseline, especially for sensitive operations such as fund transfers, account changes, or access to admin consoles. Enabling MFA is just the starting point. To validate that MFA is truly effective, focus testing efforts on the following areas:
- Verify that MFA is triggered for all critical actions, including logins from new devices or locations, password resets, and privileged user actions.
- Simulate bypass attempts using phishing kits, stolen tokens, or replayed one-time codes to confirm that resilience mechanisms are in place.
- Prioritize testing of phishing-resistant methods such as app-based authenticators, push notifications, and biometric-based MFA over SMS or email-based options, which are easier to exploit.
- Confirm that fallback mechanisms (e.g., backup codes, recovery options) are secured and cannot be used to circumvent primary controls.
- Verify that MFA is triggered for all critical actions, including logins from new devices or locations, password resets, and privileged user actions.
Strong MFA testing ensures that even if a user’s password is compromised, attackers hit friction, alerts are triggered, controls activated, and access is blocked.
- Biometric Verification Testing
Biometrics such as facial recognition, fingerprint scanning, or voice matching are increasingly used in financial applications for both convenience and security. Effective biometric authentication depends on rigorous checks across these key dimensions:
- Validate biometric login systems across different devices, operating systems, and environmental conditions (e.g., lighting, background noise).
- Test for spoofing resilience by using synthetic fingerprints, photos, or voice recordings to try and bypass the system.
- Assess the system’s liveness detection capabilities to ensure it can distinguish between a real human and a static image or video replay.
- Check how biometric data is transmitted and stored, confirming it is encrypted at rest and in transit, and not accessible via client-side manipulation.
- Validate biometric login systems across different devices, operating systems, and environmental conditions (e.g., lighting, background noise).
Done right, biometric testing closes the gap between user experience and system integrity, without opening new risk channels.
- Session Management Security
Session controls are critical in financial systems because a secure login means nothing if a session can be hijacked, extended indefinitely, or reused. Session testing should cover all points where session state and control can be exploited:
- Simulate session hijacking attempts, such as stealing tokens via man-in-the-middle attacks, cross-site scripting (XSS), or intercepting insecure storage.
- Validate session expiration policies, ensuring sessions automatically time out after inactivity and are terminated across all devices after logout or credential changes.
- Test for token reuse and confirm that expired or invalidated tokens cannot be used again.
- Launch brute-force attempts on session tokens or session IDs to ensure the system resists token prediction and rate-limits unauthorized access.
- Simulate session hijacking attempts, such as stealing tokens via man-in-the-middle attacks, cross-site scripting (XSS), or intercepting insecure storage.
These tests are especially important in environments governed by PCI DSS and DORA, which demand continuous enforcement of session integrity.
- Credential Storage Security Testing
The way credentials are stored is a major focus area for both attackers and regulators. These test cases target the weak links in how credentials are protected and stored:
- Verify that passwords are stored using modern hashing algorithms (e.g., bcrypt, Argon2) with proper salting and stretching.
- Ensure that no credentials are stored in plaintext—not in databases, logs, backups, or error messages.
- Simulate common mistakes like exposing passwords in HTTP requests or including sensitive parameters in URLs or JavaScript.
- Confirm that access to stored credentials is tightly restricted to only the systems or services that need them, with full audit logging in place.
- Verify that passwords are stored using modern hashing algorithms (e.g., bcrypt, Argon2) with proper salting and stretching.
Robust credential storage testing ensures that even if attackers breach your perimeter, they hit a wall.
Authorization Testing
Authorization testing is the process of confirming that every user whether a customer, employee, contractor, or system can only access the specific data and functions they’re allowed to, and nothing more. It’s about drawing strict lines between what different roles are permitted to do, then rigorously testing those boundaries.

Regulatory frameworks such as SOX, PCI DSS, and DORA place heavy emphasis on access control, and auditors increasingly expect evidence of robust testing, documentation, and remediation for authorization issues. The FCA and FINRA have repeatedly identified weak access boundaries as a root cause in major cybersecurity and fraud cases, with guidance stating that “segregation of duties and least privilege are foundational.”
To meet these expectations and reduce risk exposure, organizations must address authorization at multiple levels. Below are the pillars of effective authorization testing.
- Privilege Escalation Prevention
The most dangerous failures in authorization are those that allow privilege escalation, when a lower-level user or system account gains access to admin functions or sensitive data. This is a favorite tactic of attackers, insiders, and automated malware, and it’s often the starting point for broader compromise. To assess whether privilege boundaries are truly enforced, focus testing on the following areas:
- Attempt to use standard user accounts to access protected endpoints, such as admin APIs, back-office tools, or internal configuration consoles.
- Leverage role manipulation (e.g., changing user role parameters in local storage or HTTP requests) to bypass UI controls.
- Use automated security tools and RBAC (Role-Based Access Control) mapping to verify that each role only has the minimum permissions required.
- Simulate API token tampering or horizontal privilege escalation (e.g., user A accessing user B’s account via ID manipulation).
Testing privilege escalation helps you find hidden cracks in your access architecture, often where business logic and technical enforcement fail to align.
- Attempt to use standard user accounts to access protected endpoints, such as admin APIs, back-office tools, or internal configuration consoles.
- Segregation of Duties Validation
Segregation of duties (SoD) is one of the most essential internal controls in finance. It ensures that no single individual has too much control over a transaction or process, especially when money is involved. To confirm that SoD enforcement is working across your organization:
- Simulate scenarios where users are assigned overlapping roles, such as submitting and approving financial transactions, or provisioning and auditing access.
- Confirm that approval workflows include separate, accountable actors with no role overlap.
- Validate that role inheritance or permissions creep (where access accumulates over time) does not break SoD rules.
- Conduct periodic access reviews and cross-reference roles with organizational charts to catch policy violations.
- Simulate scenarios where users are assigned overlapping roles, such as submitting and approving financial transactions, or provisioning and auditing access.
Regulators like the SEC and SOX auditors expect to see not only that SoD exists in theory, but that it is tested and enforced in practice. Automated SoD testing tools and role matrices can help scale this process across complex organizations.
- Transaction Approval Workflows
Transaction approvals are a common point of failure when business logic doesn’t align with access control logic. Without proper testing, users may find unexpected paths to initiate, approve, or reverse transactions in ways that violate company policy or bypass oversight. To validate the integrity of transaction approval flows:
- Simulate multi-step transactions and verify that each step enforces the right roles, limits, and time constraints.
- Try to bypass approval stages through direct API calls, UI manipulation, or form injection.
- Validate transaction rollback or reversal logic, ensuring it can’t be abused to hide fraudulent activity.
- Test escalation thresholds (e.g., when a transaction exceeds a monetary limit and must be approved by a higher authority) to confirm they are enforced across all channels, web, mobile, internal systems.
- Simulate multi-step transactions and verify that each step enforces the right roles, limits, and time constraints.
Transaction flow testing is particularly important under PCI DSS, SOX, and FCA rules, where organizations must demonstrate that business-critical actions cannot be completed without appropriate authorization and traceability.
- Account Access Limitations
Least privilege is a foundational principle of authorization. Users should have only the access necessary to do their job and nothing more. This includes both restricting access to sensitive data and limiting available system functions. To confirm that user and system access is properly restricted:
- Create test accounts with varying roles (customer, analyst, support, admin) and verify that each can access only their intended views and functions.
- Test for horizontal access control flaws, where one user might access another’s data simply by modifying a URL or request parameter.
Review data masking policies for partial access scenarios e.g., customer service can see account balances but not full transaction history or personal identifiers.
- Simulate changes in roles (e.g., promotion or transfer) to validate dynamic permission updates and revocation.
In multi-tenant systems, this also means ensuring strict tenant isolation, so that data leaks cannot occur between organizations or business units. Auditors reviewing compliance with DORA, GDPR, and FINRA will expect to see clear documentation of how access rights are enforced, monitored, and adjusted over time.
- Create test accounts with varying roles (customer, analyst, support, admin) and verify that each can access only their intended views and functions.
Data Security Testing
Whether it’s personally identifiable information (PII), account balances, transaction records, or payment credentials, this data must be protected at all times. Data security testing ensures confidential information stays secure in storage, in transit, and in use.
Financial institutions face constant pressure from sophisticated cyberattacks, insider threats, and compliance regulators. A single exposure of sensitive data can trigger not just financial penalties, but regulatory investigations, loss of licenses, and irreversible customer distrust.
To ensure compliance and maintain trust, financial organizations must conduct multi-layered, evidence-driven testing of their data protection posture. Below are the critical areas of focus.
- Encryption Standards Verification
Encryption is the most widely accepted method for protecting data, but it only works when applied consistently and configured securely. To verify that encryption is working as intended across your systems:
- Confirm that data at rest, including database fields, file storage, logs, and backups, is encrypted using strong algorithms such as AES-256 or better.
- Verify that data in transit between applications, internal systems, and external providers is protected using TLS 1.2 or higher.
- Inspect key management systems for weak practices, such as hardcoded encryption keys, outdated algorithms, or poorly protected private keys.
- Test for certificate misconfiguration, expired certificates, or gaps in the certificate trust chain.
- Confirm that data at rest, including database fields, file storage, logs, and backups, is encrypted using strong algorithms such as AES-256 or better.
Validate that decryption events are logged, and access to decryption functionality is role-restricted and auditable.
Encryption failures are reportable events under regulations like GDPR, PSD2, and DORA. Strong encryption testing shows that your organization uses cryptography responsibly and accountably.
- Sensitive Data Masking Functionality
Testing environments often mirror production, which introduces a major risk of production data leaking into non-production systems. To ensure that masking controls are consistently applied:
- Verify that production data used for testing, development, or analytics is properly masked or anonymized in transit and at rest.
- Confirm that masking logic covers all sensitive fields, including names, PANs, SSNs, CVVs, and contact details.
- Inspect logs, debugging output, error messages, and UI screens for residual unmasked data.
- Test backup and restore operations to ensure masking isn’t inadvertently reversed or skipped during recovery.
- Simulate unauthorized access to test environments and confirm that even if breached, real data is not exposed.
- Verify that production data used for testing, development, or analytics is properly masked or anonymized in transit and at rest.
Under GDPR and PCI DSS, masking is not optional—it’s a required control wherever production data is not absolutely necessary.
- Database Security Testing
Databases are the heart of most financial systems and a frequent target in cyberattacks. To assess the resilience of your database environments:
- Review role-based access control (RBAC) policies to confirm that only authorized users and applications can query, write, or administer databases.
- Test for default credentials, overprivileged accounts, or hardcoded passwords, especially in cloud or containerized environments.
- Inspect audit logging to verify that database actions are fully captured, time-stamped, and immutable, including failed login attempts, schema changes, and access to sensitive records.
- Validate that database backups are encrypted and securely stored, and that only authorized roles can access or restore from them.
- Simulate common attack patterns such as SQL injection, unindexed queries, or misconfigured stored procedures to ensure protections are in place.
- Review role-based access control (RBAC) policies to confirm that only authorized users and applications can query, write, or administer databases.
Modern data security testing must also include cloud-native database platforms like Amazon RDS, Azure SQL, and Snowflake, accounting for unique risks like cross-tenant data leakage or API misconfigurations.
- Data Leakage Prevention Testing
Even with strong encryption and access controls, data can still leak through logs, APIs, error messages, browser caches, and third-party tools. To reduce the risk of silent exposures:
- Scan environments for sensitive data exposure in logs, HTTP requests/responses, user interfaces, and source code repositories.
- Simulate leak paths such as data embedded in URLs, cached browser fields, or system error dumps.
- Use detection tools to find PII or payment data in open cloud buckets, misconfigured object storage, or shared development spaces.
- Review API responses to ensure data minimization is returning only the required fields based on role or request context.
- Confirm that DLP (data loss prevention) rules are enforced at critical points such as email, file uploads, chat interfaces, and endpoints.
- Scan environments for sensitive data exposure in logs, HTTP requests/responses, user interfaces, and source code repositories.
Financial firms must show that data stays protected even under operational stress. Regulators increasingly expect automated scans and routine prevention controls throughout the software lifecycle.
Transaction Security Testing
A transaction is a legally binding, auditable event. Whether it’s a wire transfer, securities trade, loan disbursement, or digital payment, every transaction must be genuine, authorized, tamper-proof, and traceable.
Transaction security testing ensures that systems process only valid, properly initiated transactions, that they cannot be modified or spoofed, and that each event leaves behind an irrefutable trail of evidence. In high-stakes environments like retail banking, investment platforms, and cross-border payments, the ability to guarantee transactional integrity is a core regulatory requirement.
Regulators such as the FCA, the EU under DORA, and the PCI DSS Council have made it clear that financial institutions must actively test and prove the security, non-repudiation, and fraud resistance of every step in the transaction lifecycle. Below are the key testing pillars necessary to meet that standard.
- Transaction Integrity Validation
Every transaction in a financial system must be valid, authentic, and complete. That means it’s initiated by an authorized party, processed through the proper channels, and recorded exactly as it happened. To confirm that transactions are processed correctly and without tampering:
- Simulate legitimate and malformed transaction requests, verifying that only well-formed, authenticated transactions are accepted.
- Test message integrity controls, such as cryptographic checksums, HMACs, and digital signature validation, across APIs and internal processing layers.
- Perform end-to-end workflow validation, ensuring that transaction data is consistent and unchanged across initiation, routing, approval, and settlement stages.
- Inspect transaction logs and audit trails for completeness and accuracy, ensuring that metadata such as timestamps, user IDs, and channel data are properly captured.
- Simulate legitimate and malformed transaction requests, verifying that only well-formed, authenticated transactions are accepted.
Transaction integrity testing must produce auditable, defensible evidence. You must be able to prove it.
- Non-Repudiation Controls
Non-repudiation ensures that once a transaction is performed, the originator cannot deny having authorized it. In financial applications, this protects both the institution and the customer. To establish strong non-repudiation:
- Verify that all transactions are tied to authenticated identities, using strong methods such as MFA, device fingerprinting, or biometrics.
- Test the implementation of digital signatures or cryptographic hashes applied at transaction initiation, ensuring the signature is unforgeable and tamper-evident.
- Confirm that secure, immutable audit logs record each transaction step, from submission to processing to confirmation, along with all related metadata.
- Test system behavior in scenarios where transaction acknowledgments are interrupted or delayed, ensuring they are eventually reconciled and logged.
- Verify that all transactions are tied to authenticated identities, using strong methods such as MFA, device fingerprinting, or biometrics.
Non-repudiation is a legal requirement. Systems must produce undeniable proof of who did what, and when.
- Fraud Detection System Testing
Fraud detection systems are designed to catch transactions that are technically valid but behaviorally suspicious. These systems must be tested to ensure accuracy and readiness. To validate fraud detection capabilities:
- Inject synthetic fraudulent transactions (e.g., unusual locations, high-velocity transfers, known fraud patterns) to evaluate detection coverage.
- Perform red-teaming exercises to simulate insider fraud, stolen credentials, or coordinated attacks, and observe system response.
- Validate alerting and escalation mechanisms, ensuring suspicious activity is flagged, logged, and routed to response teams in real-time.
- Measure the false positive rate under various conditions and tune thresholds to balance detection strength and user experience.
- Test how systems handle edge cases like fragmented payments, round-dollar anomalies, or behavior masking techniques.
- Inject synthetic fraudulent transactions (e.g., unusual locations, high-velocity transfers, known fraud patterns) to evaluate detection coverage.
- Transaction Limit Validation
Transaction limits, whether per-user, per-account, or per-channel, are key to preventing fraud and enforcing policy. To ensure that limits are effective and enforced consistently:
- Attempt to exceed daily, per-transaction, and aggregate limits using standard interfaces, APIs, or indirect manipulation (e.g., splitting large payments).
- Test for race conditions or loopholes that allow multiple transactions to bypass cumulative thresholds.
- Validate enforcement of approval thresholds, such as requiring secondary authorization for high-value or unusual transactions.
- Review and test parameterized controls, confirming that limits adjust dynamically across user types, account categories, and transaction modes.
- Attempt to exceed daily, per-transaction, and aggregate limits using standard interfaces, APIs, or indirect manipulation (e.g., splitting large payments).
Limits only work if they’re enforced without exception. That’s why they must be actively tested in every core financial workflow.
Performance and Reliability Testing
Whether it's a consumer checking their account on payday or a trader executing a high-frequency order, users expect instant, uninterrupted access. Regulators expect resilience. And the business depends on both.
Performance and reliability testing ensures that your financial applications remain fast, stable, and available, even under the most demanding conditions. It’s about preparing for real-world events before they happen, from traffic spikes to infrastructure failures to third-party outages. If your systems can’t stay up, scale up, or bounce back, you’re risking compliance failures, reputational damage, and customer trust.
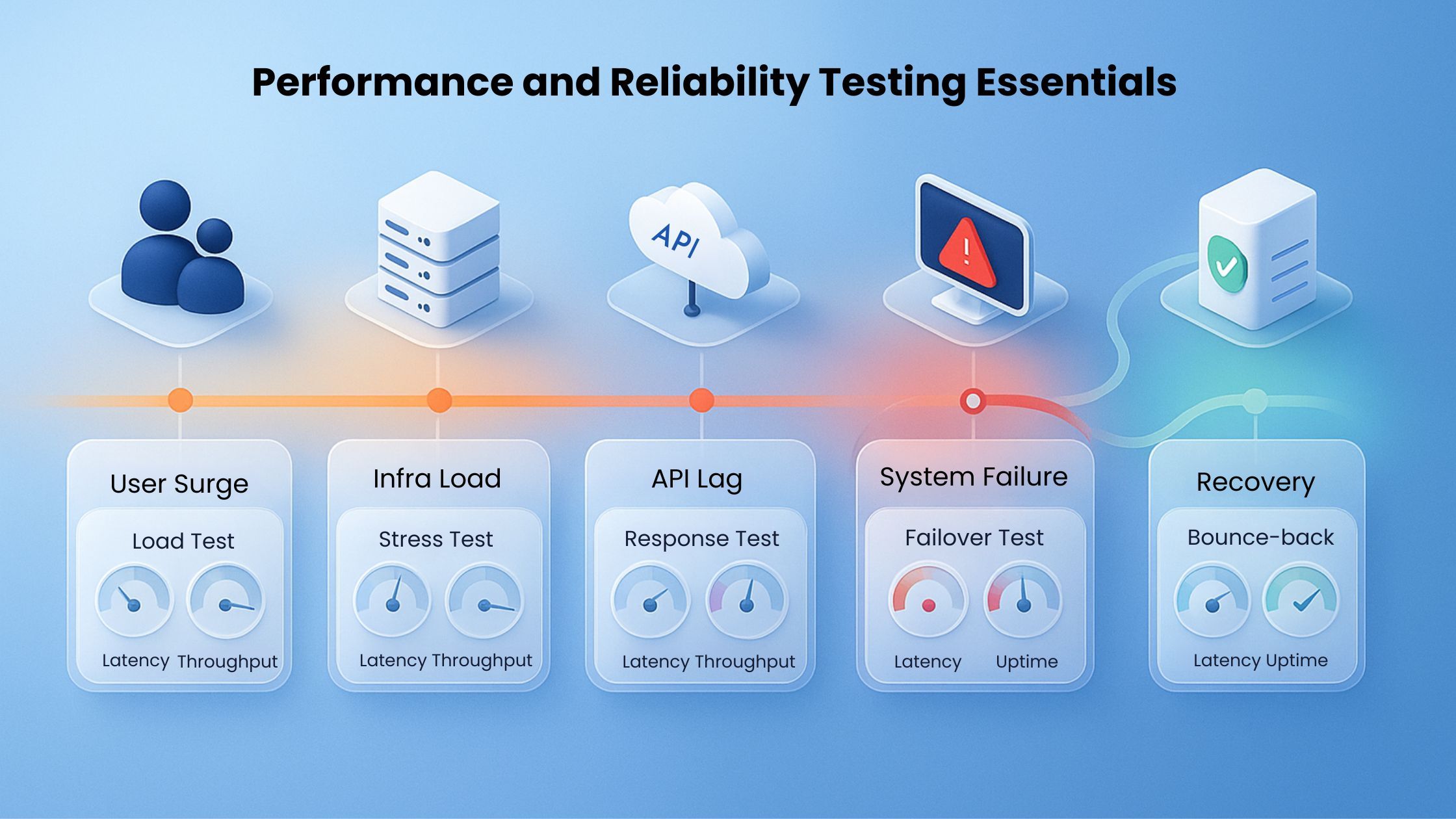
Below are key testing domains every financial organization must master to achieve high performance and regulatory-grade resilience.
- Load Testing for Peak Transaction Periods
Load testing simulates the expected transaction volumes your system is likely to face during normal but high-traffic events. In finance, these peaks are predictable and frequent: month-end account reconciliations, payroll processing days, market open/close windows, or promotional offers that drive mass user engagement. To validate readiness for real-world surges in usage:
- Simulate thousands to millions of concurrent users, using load generation tools to mimic real customer behavior and transaction types.
- Validate how the system handles session creation, login authentication, API calls, database queries, and transaction queues under heavy load.
- Identify performance issues across application tiers, database queries, middleware layers, and APIs.
- Track key metrics like response time, throughput, error rate, and resource utilization (CPU, memory, disk I/O) as load scales.
- Simulate thousands to millions of concurrent users, using load generation tools to mimic real customer behavior and transaction types.
Testing under realistic peak conditions identifies whether systems can meet SLA/SLO targets, and where stress cracks form before your customers or regulators do.
- Stress Testing for Market Volatility Scenarios
Stress testing pushes your systems beyond normal thresholds to observe how they behave under extreme pressure. This is critical in financial markets, where volatility and volume spikes are often triggered by unpredictable external events. To assess system resilience under extreme conditions:
- Simulate surge scenarios that rapidly spikes in transaction volume, increases in data requests, or concurrent jobs triggered by market events.
- Overload infrastructure to test failover logic, application throttling, and degradation handling (e.g., circuit breakers, queue backpressure).
- Measure how the system degrades. Does it fail gracefully, prioritize high-value operations, or collapse entirely?
- Observe alerting and monitoring tools under duress. Do they notify engineers before systems hit a critical state?
- Simulate surge scenarios that rapidly spikes in transaction volume, increases in data requests, or concurrent jobs triggered by market events.
Stress testing helps teams understand and extend the upper bounds of performance and verify that control remains intact when volatility strikes.
- Failover and Disaster Recovery Testing
Even the best-built systems will eventually fail. What matters is how fast you recover. Failover and disaster recovery (DR) testing ensures critical financial services remain available or can quickly return to service during outages, cyberattacks, or infrastructure disruptions. To ensure recovery capabilities are functional and compliant:
- Simulate failure scenarios: primary data center outage, network partition, storage failure, or cloud region unavailability.
- Test failover processes for critical systems, ensuring replication, switchover, and load balancing happen within your RTO (Recovery Time Objective).
- Validate data consistency and durability across failover boundaries. No duplicate, missing, or out-of-sequence transactions should occur.
- Run annual DR drills and incident response exercises, including cross-team rehearsals, escalation paths, and regulatory reporting workflows.
- Simulate failure scenarios: primary data center outage, network partition, storage failure, or cloud region unavailability.
Failover testing is as much about business continuity as it is about technology. Supervisory bodies expect organizations to prove for real-world resilience.
- Third-Party Integration Reliability Testing
Modern financial platforms depend on ecosystems. Payment gateways, AML tools, KYC services, and data providers are external systems your business can’t function without. If they fail, your services do too. To assess the reliability of third-party dependencies:
- Validate SLAs and API uptime guarantees through synthetic monitoring, dependency tracking, and alerting on latency or service degradation.
- Simulate scenarios where external systems return errors, time out, or return corrupted data, and test how your system handles it.
- Test fallback behavior: Can transactions proceed without certain services? Are users appropriately notified? Are failures logged and reported?
- Perform business continuity drills with key vendors and partners to confirm joint response plans and handoff expectations.
- Review integration points for security vulnerabilities, such as insecure token storage, misconfigured permissions, or lack of rate-limiting.
- Validate SLAs and API uptime guarantees through synthetic monitoring, dependency tracking, and alerting on latency or service degradation.
Regulators now require demonstrable assurance of third-party resilience. It’s not enough to trust your partners. You must validate their role in your availability strategy.
Special Testing Considerations
Certain business functions carry extraordinary compliance pressure and operational risk exposure. These are areas where even minor failures can lead to major fines, disrupted operations, and irreversible reputational harm.
While every part of a financial system must be secure, these areas demand specialized, rigorous, and frequently audited testing:
Each of these domains is also a regulated process that must be demonstrably secure, accurate, and resilient. Testing here is critical for risk management, audit readiness, and institutional credibility.
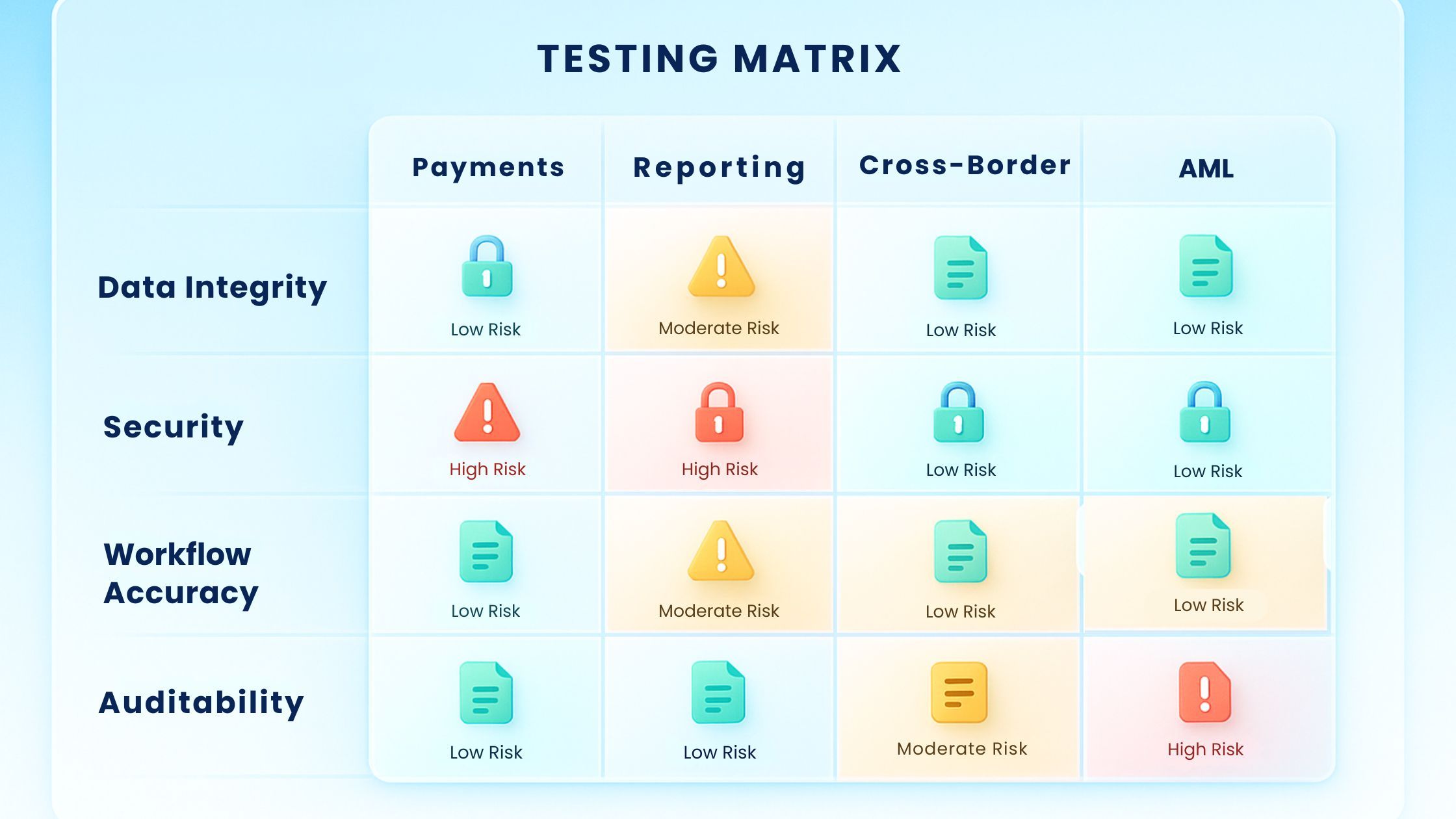
- Payment Processing Validation
Secure and compliant payment processing is at the center of every consumer-facing financial platform. Whether processing card payments, digital wallets, or direct bank transfers, institutions must protect cardholder data, ensure transaction authorization, and align with PCI DSS 4.0 and related standards. To ensure payment processing remains both secure and compliant:
- Verify that Primary Account Numbers (PANs) are masked and that CVV codes are never stored at rest, in logs, or in transient storage.
- Confirm that payment data is encrypted end-to-end, in memory, during transmission, and in any temporary buffers.
- Validate payment workflows across edge cases, including retry scenarios, multi-step authentication failures, or malformed input.
- Ensure multi-factor authentication (MFA) is enforced for operations involving stored payment credentials or high-value transfers.
- Test for error handling and data leakage, confirming that sensitive details are not exposed in logs, exception messages, or client-facing UI flows.
- Verify that Primary Account Numbers (PANs) are masked and that CVV codes are never stored at rest, in logs, or in transient storage.
These tests are essential to comply with PCI DSS 4.0, prevent financial loss, and avoid regulatory penalties following a breach.
- Regulatory Reporting Functionality
Financial institutions are required to report specific events, transactions, and operational details to regulators in a timely, accurate, and verifiable manner. To validate reporting workflows and ensure audit readiness:
- Confirm that required regulatory reports are automatically generated on schedule, with complete, accurate, and untampered data.
- Validate the end-to-end reporting pipeline from data capture through transformation, enrichment, approval, and submission.
- Ensure that audit trails are immutable, timestamped, and traceable, including evidence of internal review and submission authority.
- Test for data mapping accuracy, especially in regulatory fields that aggregate or normalize complex transaction data.
- Simulate system failures or anomalies and confirm that reporting outputs remain intact and timely.
- Confirm that required regulatory reports are automatically generated on schedule, with complete, accurate, and untampered data.
Firms must show full control over regulatory reporting, with tested controls and clean audit trails as part of routine compliance assessments.
- Cross-Border Transaction Compliance
Financial applications that support international payments or investments must comply with a patchwork of jurisdiction-specific regulations. To ensure cross-border transactions are handled legally and securely:
- Validate that currency conversions follow regulated exchange rates and rounding rules and are logged correctly across ledgers.
- Test systems for the enforcement of transaction limits, sanctions screening, and tax obligations specific to destination or origin countries.
- Simulate international transaction routes and confirm enforcement of data residency requirements (e.g., GDPR, DPDP Act, PDPA).
- Ensure that prohibited transfers to or from high-risk jurisdictions or restricted entities are flagged or blocked.
- Review audit trails to verify that cross-border activity is logged, timestamped, and tied to authenticated user identities.
- Validate that currency conversions follow regulated exchange rates and rounding rules and are logged correctly across ledgers.
Errors in this area can result in fines or loss of international transaction privileges. Testing is essential to demonstrate jurisdictional awareness and compliance control.
- Anti-Money Laundering (AML) Functionality Testing
AML systems must detect, flag, and report suspicious financial behavior. These systems are under intense scrutiny and must be validated continuously. To test AML effectiveness:
- Inject synthetic suspicious transactions (e.g., smurfing, structuring, account hopping) to evaluate detection accuracy.
- Confirm that threshold- and behavior-based detection rules operate correctly across diverse user profiles and transaction types.
- Verify that alerts are escalated and reviewed within required timeframes, with full investigation audit logs maintained.
- Test Suspicious Activity Report (SAR) workflows from initial flag to final submission, including reviewer annotations and metadata.
- Ensure independent audits of AML platforms and that test coverage reflects evolving crime typologies and regulatory guidance.
- Inject synthetic suspicious transactions (e.g., smurfing, structuring, account hopping) to evaluate detection accuracy.
Effective AML testing must reflect real-world criminal strategies to prove that the system evolves as threats do.
- Know Your Customer (KYC) Process Validation
KYC is a primary control for preventing identity fraud, money laundering, and other forms of financial abuse. To ensure onboarding and verification are secure and compliant:
- Simulate account creation with fake, expired, or manipulated documents to test document verification efficacy.
- Validate screening for Politically Exposed Persons (PEPs) and sanctioned entities, ensuring hits trigger appropriate escalation.
- Confirm that KYC data is encrypted, access-controlled, and logged to prevent misuse or unauthorized retrieval.
- Pen-test document upload and biometric flows for resistance to spoofing, injection, or bypass attempts.
- Validate ongoing re-verification policies and ensure account restrictions activate when risk indicators change.
- Simulate account creation with fake, expired, or manipulated documents to test document verification efficacy.
Robust KYC testing prevents bad actors from entering your system and proves to regulators that your front-door defenses are both current and effective.
Compliance Documentation and Reporting
Technical security controls alone aren’t enough. Financial institutions must be able to prove that those controls exist, are tested regularly, and that any gaps are discovered, tracked, and remediated in a systematic way. This is the purpose of compliance documentation and reporting that provides a defensible, auditable trail of every control, test, and action that supports a secure and compliant environment.
From PCI DSS 4.0 to DORA, GDPR, and FINRA, regulators now require evidence of risk management. That means clear documentation of what was tested, what was found, how it was fixed, and when it was verified. Without this, even technically sound security programs can fail an audit or trigger penalties.
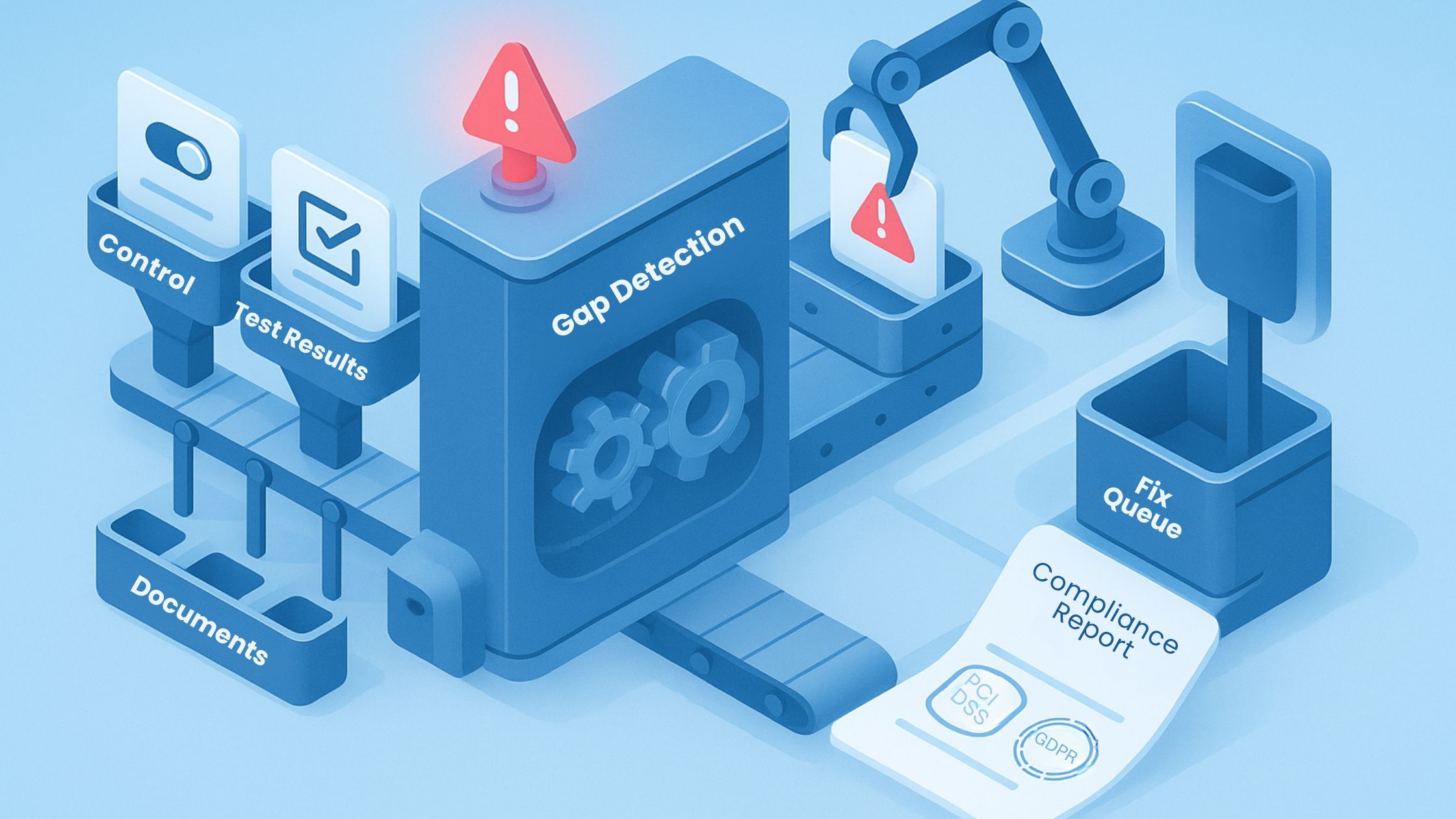
The following practices form the foundation of a compliance program that is functional and demonstrably resilient, organized, and audit-ready.
Evidence Collection Methodology
Documentation begins with evidence collection, like capturing proof that controls are in place, working correctly, and continuously maintained. It’s not enough to say a test was run or a vulnerability was fixed. You need to be able to show it. To build a strong, audit-ready evidence trail:
Collect and archive raw evidence from each test and remediation event, including:
- Screenshots of configuration settings.
- Log file excerpts.
- Tool output from vulnerability scans or penetration tests.
- Ticket references showing remediation steps and validation.
- Audit trail entries proving access control enforcement or transaction logs.
- Store evidence in a centralized, secure repository, ideally within a GRC (Governance, Risk, and Compliance) tool, where it can be easily retrieved during audits or regulator inquiries.
- Automate evidence capture where possible, e.g., exporting CI/CD pipeline results, generating time-stamped reports from scanners, or auto-archiving configuration change logs.
- Ensure all evidence includes metadata: who ran the test, when it was conducted, what environment it applied to, and what risk category it addressed.
The expectation now is not just “show us the results,” but “show us your ability to prove the results.” Without robust evidence practices, audit readiness becomes reactive and inconsistent.
Compliance Test Reporting Templates
Clear, consistent reporting transforms raw evidence into structured compliance documentation. A well-structured test report communicates what was tested, why it matters, what was found, and what was done about it. To ensure reports meet both internal and regulatory needs:
- Standardize formats for all security reports, including penetration tests, vulnerability assessments, control audits, third-party assessments, and code reviews.
- Include these key elements in every report:
- Scope of testing, including systems, environments, and controls assessed.
- Testing methodology, mapped to regulatory expectations (e.g., PCI DSS 11.4, DORA Annex IV)
- Findings, prioritized by severity and mapped to risks or compliance clauses.
- Remediation status, including ticket numbers or closure notes.
- Validation results, showing re-testing outcomes or mitigation justification.
- Scope of testing, including systems, environments, and controls assessed.
- Maintain version control for reports and supporting evidence. Track changes across audit cycles or after policy updates to demonstrate continuous improvement.
Templates streamline internal processes and help auditors follow your logic and ensure your testing program holds up to detailed regulatory scrutiny.
Remediation Tracking Procedures
A secure control is important but so is your ability to identify a vulnerability, fix it, and prove resolution within a defined timeframe. To manage findings and demonstrate compliance over time:
- Use a formal ticketing system (e.g., Jira, ServiceNow, or a GRC platform) to log every issue, including:
- Vulnerability description and severity.
- Regulatory mapping (e.g., “SOX Control ITGC-002”)
- Assigned owner and deadline.
- Status updates and supporting notes.
- Vulnerability description and severity.
- Track remediation timelines closely. Many frameworks (including DORA and PCI DSS 4.0) require evidence that vulnerabilities are resolved within specific time windows based on severity.
- Integrate remediation workflows with your CI/CD pipeline, if applicable, to break builds or block releases when critical vulnerabilities remain open.
- Automate post-remediation testing and attach validation results directly to the original ticket.
- Maintain a real-time dashboard showing open, closed, overdue, and reopened issues to support reporting for auditors and leadership.
Regulators focus on how quickly and effectively issues are addressed. Your documentation should provide clear evidence of ownership, progress, and completion.
Audit Preparation Guidelines
Even the best controls and reports won’t be effective if your team is unprepared for the audit process. Audit readiness means your documentation is organized, your evidence is accessible, and your team is ready to respond. To prepare for successful audits:
- Maintain an “audit binder” or centralized digital archive containing:
- Control matrices and regulatory mappings.
- Completed test reports and supporting evidence.
- Remediation dashboards and summaries.
- Organizational policies and control definitions.
- Historical audit findings and improvement logs.
- Control matrices and regulatory mappings.
- Conduct internal mock audits at least once a year. Include dry-run interviews with control owners and walkthroughs of evidence presentations.
- Assign domain-specific owners (e.g., PCI lead, SOX lead) who can speak confidently to both technical and procedural elements of their control areas.
- Maintain a changelog of continuous improvements, like what’s been updated since the last audit, and why.
- Prepare executive-level summaries for leadership and board members, including:
- Current compliance posture and risk ratings.
- Number of controls tested and results.
- Major issues resolved or in progress.
- Ongoing gaps or emerging areas of concern.
- Current compliance posture and risk ratings.
Continuous Security Assurance
The complexity of modern systems, the speed of software delivery, and the escalation of cyber threats demand an approach where security is built in.
Continuous security assurance is the process of embedding proactive, automated, and repeatable security validation into every phase of the development and operational lifecycle. This approach ensures that vulnerabilities are identified early, remediated quickly, and prevented from resurfacing. More importantly, it delivers clear evidence that controls are not just present, but functioning at all times.
Here’s how to build and maintain an effective continuous assurance model.
Automated Compliance Scanning
By embedding security and compliance checks directly into DevOps pipelines and cloud environments, organizations can identify and address risks before code even reaches production. To ensure early and reliable detection of issues:
- Integrate Static Application Security Testing (SAST) tools into development workflows to catch code-level vulnerabilities like input validation flaws or insecure API usage.
- Use dependency scanners to detect vulnerabilities in third-party libraries. Configure gates to block builds with critical CVEs unless formally approved.
- Automate Dynamic Application Security Testing (DAST) and infrastructure scans in your CI/CD processes. These tools simulate runtime attacks to uncover issues like broken authentication or misconfigurations.
- Deploy cloud compliance scanners to monitor for misassigned privileges, open ports, exposed storage, or configuration drift. Map findings to PCI DSS 4.0, ISO 27001, and DORA requirements.
- Schedule recurring scans based on risk tier—daily, weekly, or on code merges—and configure alerts for high-priority issues.
Automated scanning improves compliance from a quarterly meeting into a built-in safeguard across your delivery lifecycle.
Penetration Testing Schedule
Automation covers routine checks, but human-driven penetration testing is essential for uncovering complex, logic-based, or chained vulnerabilities that tools miss. To ensure adequate and timely test coverage:
- Establish a baseline schedule that includes:
- Annual full-scope penetration tests across applications and infrastructure.
- Quarterly targeted tests on high-risk components.
- Ad-hoc testing after major feature rollouts, architecture changes, or security incidents.
- Annual full-scope penetration tests across applications and infrastructure.
- Align testing cadence with regulatory mandates:
- DORA requires threat-led penetration testing every three years for critical ICT systems.
- FINRA recommends continuous and adversarial testing.
- PCI DSS 4.0 mandates annual and post-change penetration testing.
- DORA requires threat-led penetration testing every three years for critical ICT systems.
- Extend test coverage beyond web apps to include APIs, identity platforms, backend services, and third-party dependencies.
- Use internal red teams, external specialists, or bug bounty programs to simulate advanced adversaries.
- Capture detailed findings, remediation evidence, and retesting results, and integrate them into compliance documentation.
Penetration testing provides a layer of depth and realism that automation cannot.
Vulnerability Management Processes
Continuous assurance only works if vulnerabilities are triaged, resolved, and verified through disciplined, trackable processes. To manage vulnerabilities with speed and precision:
- Centralize findings from scanners, manual reviews, and penetration tests into a single tracking platform.
- Tag each entry with a unique ID, CVSS score, affected assets, and relevant compliance mappings (e.g., PCI 6.1, DORA Annex II).
- Assign owners and remediation deadlines according to severity:
- Critical: within 7 days.
- High: within 14 days.
- Medium: within 30 days.
- Low: backlog or scheduled review.
- Critical: within 7 days.
- Attach validation evidence to each closure, such as scan reports, screenshots, or patch logs.
- Maintain dashboards that show trends in open, closed, and aging vulnerabilities. Share with leadership and risk committees monthly.
- Use risk review cycles or security sprints to resolve blockers and maintain accountability across departments.
Effective vulnerability management ensures that issues don’t just get logged and they get fixed, verified, and documented.
Security Regression Testing Strategies
Frequent changes increase the risk of reintroducing old vulnerabilities. Security regression testing prevents this by validating that past fixes still hold true in new builds. To build a resilient regression testing approach:
- Create automated security tests for critical controls including:
- Authentication and session expiration.
- Role-based access control.
- Input sanitization.
- Key business logic flows.
- Authentication and session expiration.
- Embed these tests into CI/CD pipelines. Configure them to fail builds if key controls break.
- Maintain a vulnerability regression list. It is a reference to previously remediated issues. Use it to prioritize areas for revalidation in major releases.
- Leverage behavioral snapshots or traffic replay tools to confirm expected system behavior post-deployment.
- Run manual regression sweeps after large dependency updates or permission model changes, especially for high-risk features.
Conclusion
Security testing in financial applications is an ongoing commitment to resilience, accountability, and trust. As this guide has shown, regulatory expectations are more demanding than ever. From PCI DSS 4.0 to DORA, regulators want proof that those controls work, are tested regularly, and are fixed when they fail.
To meet this challenge, organizations need to think in layers. Start by securing access with strong authentication and authorization testing. Protect the data that powers your business. Verify every transaction, especially the ones that cross borders. Test for performance under pressure, and validate the systems that handle reporting, payments, and compliance checks.
But the real shift is trearting it like a continous process. One that gets embedded into the way software is built, tested, and improved. The organizations that rise in this new environment will be the ones that treat compliance as a blueprint for better systems.
Whether you’re a CISO, developer, compliance officer, or auditor, the message is the same: the only sustainable path forward is one where testing, documentation, and improvement never stop.
Share This Article:



